The tech industry is experiencing significant upheaval. Big Tech has made mass layoffs to cut costs, and cybersecurity companies are not immune. However, while IT budgets face scrutiny as companies cut discretionary spending, cybersecurity will remain a priority.
State-sponsored cyberattacks are likely to increase in 2023. The Russian invasion of Ukraine, a continuing trade war between the US and China, and high-profile elections are all catalysts for state-sponsored attacks.
Attacks on critical national infrastructure and supply chains will also increase in 2023. These are highly effective at causing large-scale disruption and long-lasting financial impact. For instance, in February 2023, US chipmaking equipment supplier MKS Instruments was affected by a ransomware attack that cost over $200m in lost and delayed sales.
Remote working has remained popular post-pandemic, causing a distributed workforce and increasing risks. In 2023, more companies will work to adopt a zero-trust architecture and secure distributed endpoints to contain attacks and protect the entire corporate network. Companies like Google have already adopted a zero-trust architecture, while the US federal government is in the midst of a multi-year migration to zero trust. Other companies will follow this lead to support remote working.
Market size and growth forecasts
According to GlobalData forecasts, the global cybersecurity market will be worth $334bn by 2030, having grown at a compound annual growth rate (CAGR) of 10% between 2022 and 2030. Software-based cybersecurity products will be the largest market segment, contributing 44% of total revenue in 2030, with services accounting for 39%.
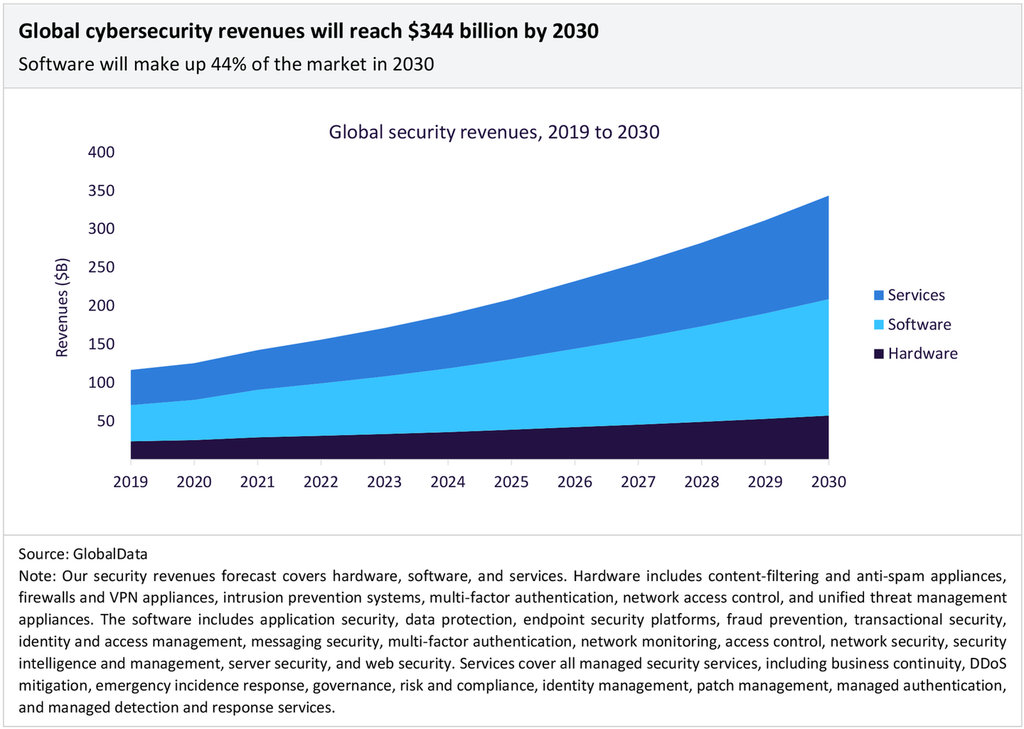
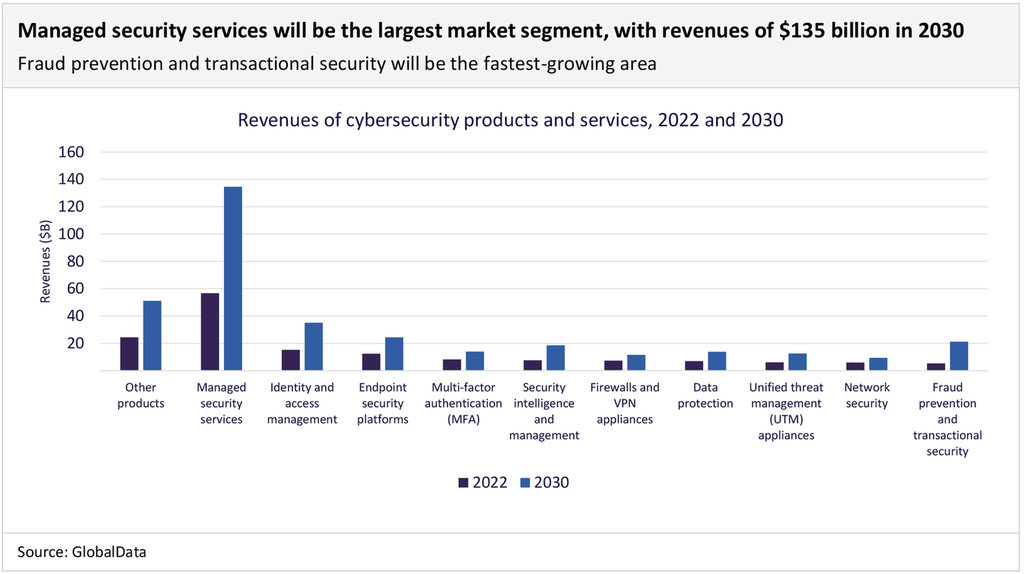
Managed security services revenues will be the largest single market segment in 2030. Revenues will increase by a CAGR of 11.4% between 2022 and 2030, reaching $135bn in 2030. Managed security services refer to services that have been outsourced to an external vendor or supplier. Companies facing a cybersecurity skills gap and a growing threat will increasingly outsource security services to external experts.
The next largest market segment will be identity and access management products. Revenues will increase at a CAGR of 11% between 2022 and 2030, reaching $35 billion by the end of the period. The rise in cloud computing and distributed workforces makes identity and access management a key preventative security measure as, according to Verizon’s 2022 Data Breach Investigations Report, 82% of all data breaches involve a human element, such as phishing or the use of stolen credentials.
Threat actors
The cybersecurity landscape is complex. Today’s always-connected world offers many opportunities for cyberattackers to disrupt countries, organisations, and individuals. The table below shows the four main types of threat actors – thieves, hacktivists, terrorists, and other malicious players.
Types of cyberattack
Cyberattacks can be split into two types: un-targeted or targeted.
Un-targeted cyberattacks
In un-targeted attacks, attackers will target as many devices, services, or users as possible. There is little direct interest in the victim because there will always be several machines or services with vulnerabilities. Attackers typically use techniques that take advantage of the internet's openness. These include:
▪ Phishing: This is the practice of sending fraudulent messages to large numbers of people asking for sensitive information (such as bank details) or encouraging them to visit a fake website.
▪ Malware: Malware, short for malicious software, refers to any intrusive software developed by cybercriminals to steal data and damage or destroy computers and computer systems. Examples of common malware include viruses, worms, spyware, adware, and ransomware.
▪ Water holing: This refers to setting up a fake website or compromising a legitimate one to exploit visiting users.
▪ Zero-day exploits: When an attack targets a security flaw previously unknown to the software vendor or security provider. Typically, an attacker will probe a system until they discover a vulnerability. If it has never been reported, it is a zero-day flaw because developers have had zero days to fix it. Taking advantage of the security flaw is a zero-day exploit, which often compromises the target system. Zero-day vulnerabilities could exist for years before they are discovered.
Phishing continues to be popular due to its simplicity and effectiveness. It targets the weakest link in the security chain: the user. Phishers usually masquerade as trustworthy entities. According to Verizon’s 2022 Data Breach Investigations Report, 82% of all data breaches involve a human element, such as phishing or using stolen credentials.
Phishing is successful because users face an information overload, making them less able to spot attacks. Cybercriminals are resourceful when deceiving users by crafting content and evading detection patterns. Cybercriminals also take advantage of the information users share about themselves through social media to create tailored and more authentic messages.
Despite all the warnings, users still possess insufficient knowledge about phishing, its use to deliver ransomware, and the best practices to deal with unknown threats. In addition, many users are simply not sufficiently sceptical when receiving requests to transfer funds, open attachments, or provide sensitive information. Even worse, some organisations do not include user training and awareness in their defence strategy.
Malware attacks can exfiltrate data in mass amounts. One of the most concerning types of malware is ransomware, which encrypts files on a device, rendering them and the systems that rely on them unusable. Cybercriminals then demand ransom in exchange for decryption.
Ransomware has been used in several high-profile attacks and is the most concerning type of cyberattack for business leaders. A ransomware attack can cause a significant loss of revenue and can paralyze an organisation. The 2022 Cybereason report, Ransomware: The True Cost to Business, revealed that 73% of organisations surveyed suffered at least one ransomware attack in 2022.
The increased complexity of ransomware attacks and the addition of measures designed to turn the screw on reluctant payers, such as pre-emptive early data exfiltration, demonstrate that cybercriminals are operating from a position of strength.
There is a link between frequently seen threat types, particularly phishing and ransomware. Phishing is the number one delivery vehicle for ransomware. Phishing emails are easy to send and yield a faster return on investment for a cybercriminal enterprise. As part of social engineering schemes, phishing lures victims into executing actions without realising the malicious intent. The less aware the targeted user is, the more fruitful the attack. Likewise, in the case of targeted attacks, phishing emails are created to look like they come from a trustworthy sender but link to or contain malicious content that executes as soon as users click it, encrypting their data and demanding a ransom.
Targeted cyberattacks
In a targeted attack, an organisation is identified because the attacker has a specific interest in its business or has been paid to target it. Planning the attack could take months as hackers look for the best route to deliver exploits directly to an organisation’s systems (or users). A targeted attack is usually more damaging than an un-targeted one because it has been specifically tailored to attack systems, processes, or personnel.
There are three main types of targeted cyberattacks:
- Spear-phishing attack: Sending messages to targeted individuals with an attachment containing malicious software or a link that downloads malicious software.
- Distributed denial of service (DDoS) attack: A coordinated attack in which multiple connected machines in a botnet, usually infected with malware or otherwise compromised to co-opt them into the attack, flood a network, server, or website with data, causing it to crash.
- Supply chain attack: An attack in which threat actors compromise enterprise networks using connected applications or services owned or used by outside partners, such as suppliers. The outside provider has already been granted the rights to use and manipulate areas of a company’s network, applications, or sensitive data, so the attacker only has to either penetrate the third party’s defences or program a loophole into a solution offered by a vendor to infiltrate the system.
Organisations’ technical complexity breeds vulnerability. Every organisation has an array of devices, networks, platforms, and infrastructure, and this complexity creates vulnerabilities. The move to remote working due to the pandemic added widespread use of collaboration tools to a mix that already included operating systems, identity and access management, multi-factor authentication, virtual machines, containers, applications, databases, storage, and middleware. The enterprise of today is complex, and a perfect environment for hackers.

GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.